Peer-to-peer protocols which scale up, down, and sideways.
 Willow is a set of protocols for running your own digital spaces. All spaces are completely independent from each other, and they can be as big or small as you want.
Willow is a set of protocols for running your own digital spaces. All spaces are completely independent from each other, and they can be as big or small as you want.
 These digital spaces are stored on your own hardware, cutting out unwanted third parties.
These digital spaces are stored on your own hardware, cutting out unwanted third parties.
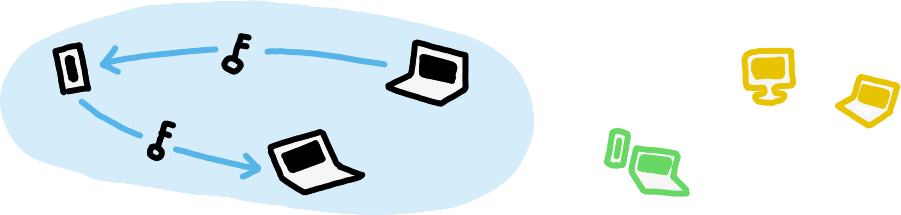 Only devices which have been given explicit consent to store data can receive it.
Only devices which have been given explicit consent to store data can receive it.
 Store any kind of data, organised in a manner similar to files and folders.
Store any kind of data, organised in a manner similar to files and folders.
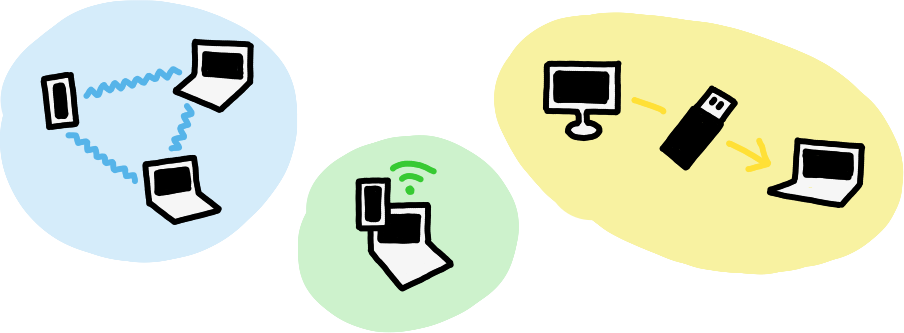 Data can travel between devices in many different ways, so you can choose the appropriate pathways, whether that's the internet or a USB key.
Data can travel between devices in many different ways, so you can choose the appropriate pathways, whether that's the internet or a USB key.
Willow
 Synchronisable data storage with destructive editing.
Synchronisable data storage with destructive editing.
- Works offline.
- Store any kind of data.
- Truly destructive editing.
- Actually delete stuff.
- End-to-end encryptable.
- Eventually consistent.
Meadowcap
 A capability system for fine-grained access control
A capability system for fine-grained access control
- No central authority needed.
- No assumptions about what an identity is.
- Owned namespaces for top-down moderation.
- Communal namespaces for bottom-up networks.
Confidential Sync
 Private and efficient synchronisation
Private and efficient synchronisation
- Encrypted communication.
- Only syncs what you're interested in.
- Only syncs what others have access to.
- Man-in-the-middle attack resistant.
- Streaming sync.
- Dainty bandwidth and memory usage.
Drop Format
 Securely deliver data by any means possible.
Securely deliver data by any means possible.
- Package Willow data in a single encrypted file.
- Move it however you want.
- Sneakernets.
- Email.
- FTP servers.
- Messaging apps.
- Dead drops.

